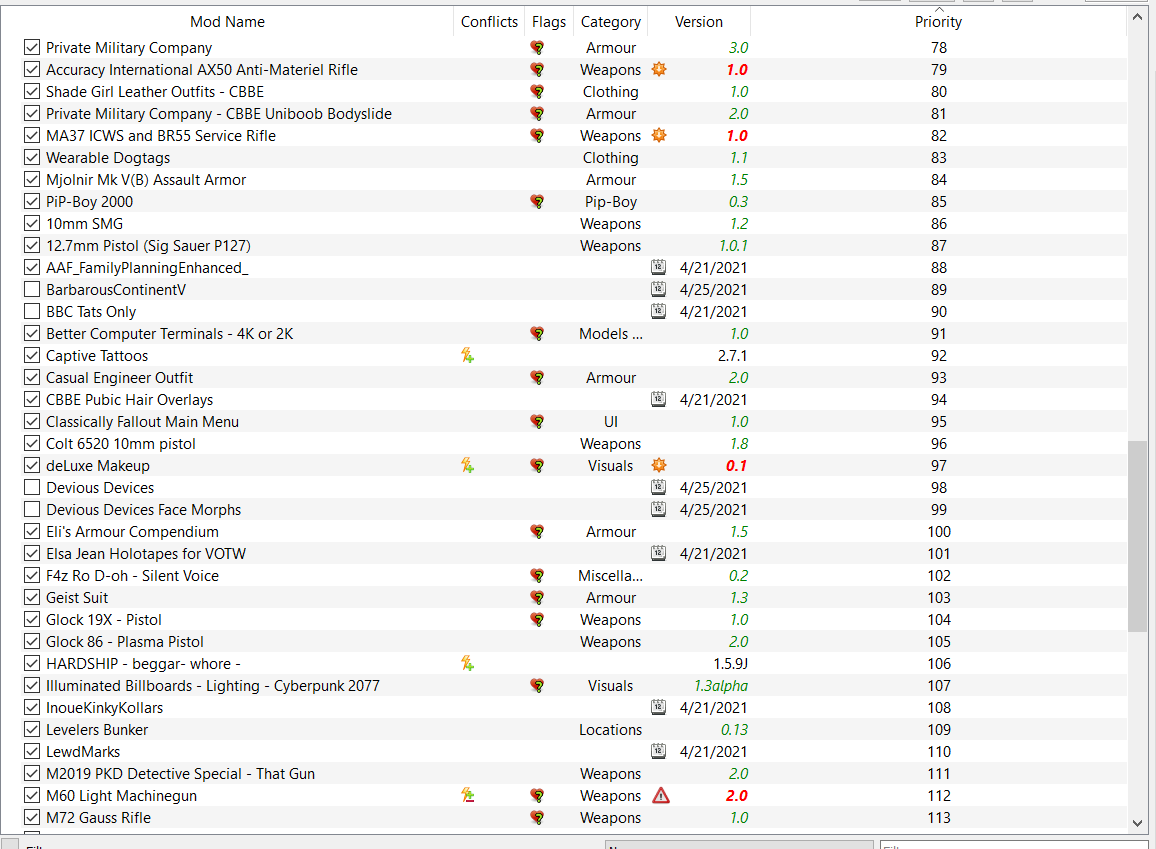
If you are looking for (Legacy) Family Planning Enhanced Assorted Addon's – Other – LoversLab you’ve came to the right page. We have 35 Pics about (Legacy) Family Planning Enhanced Assorted Addon's – Other – LoversLab like AAF Family Planning Enhanced for CBBE, Fusion Girl, and Jane Bod – Page, (Legacy) Family Planning Enhanced Assorted Addon's – Downloads and also Fallout 4 Nuclear Family Story Mission (Spoiler Alert!!!) (+ Commentary. Here you go:
Table of Contents
(Legacy) Family Planning Enhanced Assorted Addon's – Other – LoversLab

www.loverslab.com
planning family screenshots enhanced assorted legacy loverslab addon
髪・顔・体 アップデート順 – Fallout4 Mod データベース

fallout4.2game.info
(Legacy) Family Planning Enhanced Assorted Addon's – Downloads
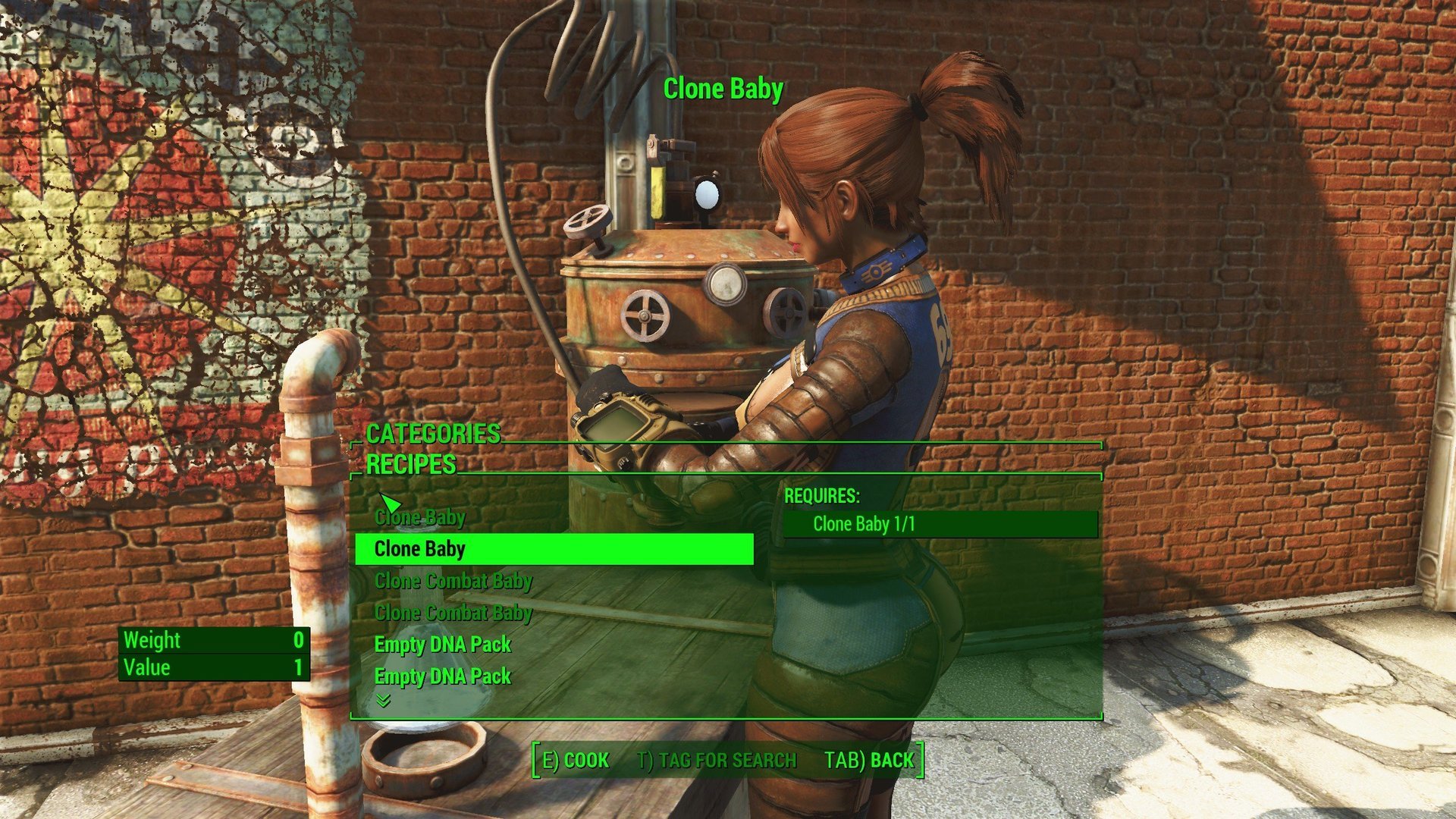
www.loverslab.com
planning family enhanced loverslab
Fallout 4 Mod Adulte / Fallout 4 Hardcore Outfit Armor Clothing

detbipolareliv.blogspot.com
Fallout4 Def_Ui 設定 – Enfys Cadogan

enfyscadogan.blogspot.com
The Family At Fallout 4 Nexus – Mods And Community

www.nexusmods.com
mods
Episode I – Family Problems At Fallout 4 Nexus – Mods And Community

www.nexusmods.com
problems family loading mods fallout episode
Loverslab Fallout 4 Family Planning Monsters – Pasewar

pasewar.weebly.com
SEARCH FOR THE FAMILY | Fallout 3 Daily | Episode 25 – YouTube

www.youtube.com
fallout shotgun terrible
Remaining Family At Fallout 4 Nexus – Mods And Community

www.nexusmods.com
family remaining information fallout
Loverslab Fallout 4 Family Planning Mesh – Gaseqa

gaseqa.weebly.com
This Fallout 4 Mod Will Make You Feel Like You're In Anime

wccftech.com
mod fallout anime mods character fallout4 fo4 game feel make nexus create re will
AAF Family Planning Enhanced For CBBE, Fusion Girl, And Jane Bod – Page

www.loverslab.com
planning family enhanced girl fusion aaf cbbe bod jane loverslab fallout4
AAF Family Planning Enhanced Redux – Page 5 – Downloads – Advanced

www.loverslab.com
loverslab
Fallout 4 | 41 FINALE | Nuclear Family – YouTube

www.youtube.com
radiation fallout
The Family | Fallout Wiki | FANDOM Powered By Wikia
fallout.wikia.com
arefu
Fallout 4 – Episode I – Family Problems – Quest Mod For Xbox & PC – YouTube

www.youtube.com
FAMILY FRIENDLY CONTENT | Fallout 4 – YouTube

www.youtube.com
fallout
Parental Guidence At Fallout 4 Nexus – Mods And Community

www.nexusmods.com
guidence parental information
Fallout 4 GAME MOD Episode I – Family Problems V.04 – Download

www.gamepressure.com
fallout problems mod episode family game created
Family Planning Enhanced Assorted Addon's – Other – LoversLab
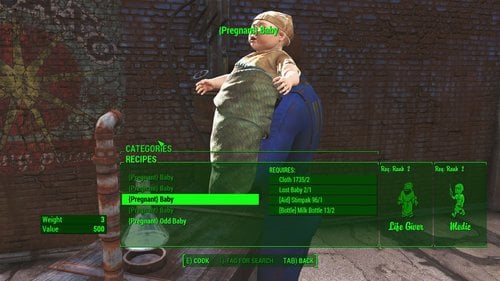
www.loverslab.com
assorted loverslab addon
(Legacy) Family Planning Enhanced Assorted Addon's – Other – LoversLab

www.loverslab.com
planning family enhanced loverslab assorted legacy screenshots aaf additional well help addon
Fallout 4 Lets Play – Episode 1 [Family] (Fallout 4 Gameplay) – YouTube
![Fallout 4 Lets Play - Episode 1 [Family] (Fallout 4 Gameplay) - YouTube](https://i.ytimg.com/vi/l2sTiujCqFg/maxresdefault.jpg)
www.youtube.com
MY FAMILY – Fallout 4 #1 – YouTube

www.youtube.com
Fallout 4 Playthrough Part 138 – Family Problems – YouTube

www.youtube.com
AAF Family Planning Enhanced Addon Pack – Sex Effects – LoversLab

www.loverslab.com
aaf loverslab planning enhanced family screenshots addon pack
Loverslab Fallout 4 Family Planning – Gasepie

gasepie.weebly.com
Fallout 4 Nuclear Family Story Mission (Spoiler Alert!!!) (+ Commentary

www.youtube.com
Fallout 4 Walkthrough Part 74 – Family Secrets – YouTube

www.youtube.com
fallout
492 Best Images About Fallout 3, New Vegas, And Fallout 4! On Pinterest

www.pinterest.com
fallout family funny
Episode I – Family Problems At Fallout 4 Nexus – Mods And Community

www.nexusmods.com
fallout mods problems episode family deep down
Loverslab Fallout 4 Family Planning How Do Addons Work – Lesshresa

lesshresa.weebly.com
Family Life At Fallout 4 Nexus – Mods And Community

www.nexusmods.com
family life information
Fallout 4 – Ending – THE NUCLEAR FAMILY ★ Let's Play Fallout 4 (Fallout

www.youtube.com
No Pregnancy Progress (Family Planning Enhanced 2.102) – Fallout 4
www.loverslab.com
Mod fallout anime mods character fallout4 fo4 game feel make nexus create re will. The family at fallout 4 nexus. Parental guidence at fallout 4 nexus
 ataylormadelife.com ataylormadelife.com adalah website berita yang memberikan informasi seputar teknologii dan games
ataylormadelife.com ataylormadelife.com adalah website berita yang memberikan informasi seputar teknologii dan games